CALL: 888-Hyper-11
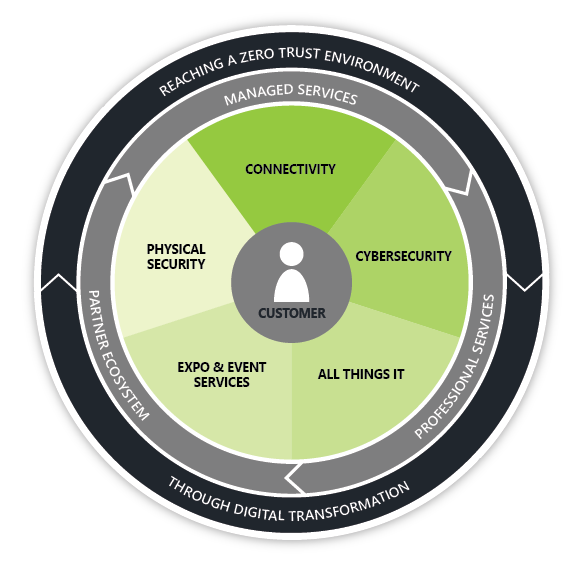
YOUR IT PARTNER IN REACHING A ZERO TRUST ENVIRONMENT
Let us manage your IT so you can focus on your business.
Learn MoreOUR SERVICES
Our Services
OUR LEADER
ABOUT HYPER NETWORKS
Since 2014 Hyper Networks has been saving businesses money while making network downtime, security concerns, and fractured IT infrastructure things of the past.
ABOUT US
LET'S WORK TOGETHER
Our customers appreciate our high-touch, quick-response support experience. And, we have a genuine passion for helping you learn. We encourage questions, work transparently, and take the time to explain not only what needs to be done but also why.
PROJECT INSIGHTS
PROJECT INSIGHTS
"Success is not final; failure is not fatal: It is the courage to continue that counts." - Winston S. Churchill





1000+ Happy Customers
5000+ Successful Projects
55 Team Members
8000+ Cups of Coffee
OUR PARTNERS
OUR VENDORS & AFFILIATES
A huge part of our success is through our channel and vendor partners. We take these seriously and strive to show this in the many ways they interact with us. We want to be easy to do business with and help our partners achieve their goals.





CONNECT WITH US
CONNECT

Henderson, NV 89052











